2024-08-20 カリフォルニア大学サンディエゴ校(UCSD)
<関連情報>
- https://today.ucsd.edu/story/computer-scientists-discover-vulnerabilities-in-a-popular-security-protocol
- https://www.blastradius.fail/pdf/radius.pdf
有害とされるRADIUS/UDP RADIUS/UDP Considered Harmful
Sharon Goldberg, Cloudflare; Miro Haller and Nadia Heninger, UC San Diego; Mike Milano, BastionZero; Dan Shumow, Microsoft Research; Marc Stevens, Centrum Wiskunde & Informatica; Adam Suhl, UC San Diego
the USENIX Security 2024 conference
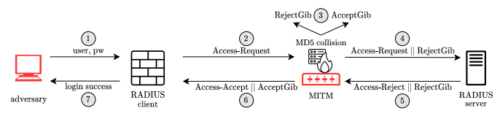
Abstract
The RADIUS protocol is the de facto standard lightweight protocol for authentication, authorization, and accounting (AAA) for networked devices. It is used to support remote access for diverse use cases including network routers, industrial control systems, VPNs, enterprise Wi-Fi including the Eduroam network, Linux Pluggable Authentication Modules, and mobile roaming and Wi-Fi offload.
We have discovered a protocol vulnerability in RADIUS that has been present for decades. Our attack allows a man-in-the-middle attacker to authenticate itself to a device using RADIUS for user authentication, or to assign itself arbitrary network privileges. Our attack exploits an MD5 chosen-prefix collision on the ad hoc RADIUS packet authentication construction to produce Access-Accept and Access-Reject packets with identical Response Authenticators, allowing our attacker to transform a reject into an accept without knowledge of the shared secret between RADIUS client and server.
We optimize the MD5 chosen-prefix attack to produce collisions online in less than five minutes, and show how to fit the collision blocks within RADIUS attributes that will be echoed back from the server. We demonstrate our attack in a variety of settings against popular RADIUS implementations. It is our hope that this attack will provide the impetus for vendors and the IETF to deprecate RADIUS over UDP, and to require RADIUS to run over secure channels with modern cryptographic privacy and integrity guarantees.



