2025-09-18 カリフォルニア大学リバーサイド校(UCR)
<関連情報>
- https://news.ucr.edu/articles/2025/09/18/ucr-computer-scientists-boost-us-cybersecurity
- https://arxiv.org/abs/2506.04453
- https://ieeexplore.ieee.org/document/11023387
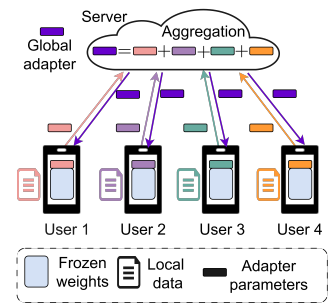
パラメータ効率的な微調整に対する勾配反転攻撃 Gradient Inversion Attacks on Parameter-Efficient Fine-Tuning
Hasin Us Sami, Swapneel Sen, Amit K. Roy-Chowdhury, Srikanth V. Krishnamurthy, Basak Guler
arXiv Submitted on 4 Jun 2025
DOI:https://doi.org/10.48550/arXiv.2506.04453
Abstract
Federated learning (FL) allows multiple data-owners to collaboratively train machine learning models by exchanging local gradients, while keeping their private data on-device. To simultaneously enhance privacy and training efficiency, recently parameter-efficient fine-tuning (PEFT) of large-scale pretrained models has gained substantial attention in FL. While keeping a pretrained (backbone) model frozen, each user fine-tunes only a few lightweight modules to be used in conjunction, to fit specific downstream applications. Accordingly, only the gradients with respect to these lightweight modules are shared with the server. In this work, we investigate how the privacy of the fine-tuning data of the users can be compromised via a malicious design of the pretrained model and trainable adapter modules. We demonstrate gradient inversion attacks on a popular PEFT mechanism, the adapter, which allow an attacker to reconstruct local data samples of a target user, using only the accessible adapter gradients. Via extensive experiments, we demonstrate that a large batch of fine-tuning images can be retrieved with high fidelity. Our attack highlights the need for privacy-preserving mechanisms for PEFT, while opening up several future directions.
地平線の彼方:誤設定されたファイアウォール背後のホストとサービスの解明 Beyond the Horizon: Uncovering Hosts and Services Behind Misconfigured Firewalls
Qing Deng; Juefei Pu; Zhaowei Tan; Zhiyun Qian; Srikanth V. Krishnamurthy
2025 IEEE Symposium on Security and Privacy Date Added to IEEE Xplore: 16 June 2025
DOI:https://doi.org/10.1109/SP61157.2025.00164
Abstract:
Public IP addresses can expose devices and services to risks such as port scanning and subsequent cyberattacks. Therefore, firewalls are extensively deployed and play a critical role in enforcing security policies and preventing unauthorized access. However, vulnerabilities can allow firewalls to be by-passed, effectively nullifying the protection. In this paper, we present the first comprehensive study of a previously understudied attack surface: firewall misconfigurations that inadvertently expose protected services to the public Internet. Specifically, we demonstrate flawed firewall rules that allow inbound connections from special source ports to bypass the firewall, and explore the prevalence and security implications thereof. To this end, we scan the IPv4 space for 15 commonly high-risk TCP and UDP services from two special source ports. Our measurement reveals the widespread existence of such misconfigurations and identified over 2,000,000 otherwise unreachable services spread over 15,837 autonomous systems, expanding the “observable Internet” for various protocols by up to 12.60%. More importantly, the affected services generally exhibit higher security risks than the publicly accessible ones, like outdated software versions and weak configurations. Despite the severity of this vulnerability, our honeypot experiment provides little evidence of active exploitation in the wild. Our findings offer insights for better security posture and network administration, helping researchers and organizations anticipate and mitigate potential cyber threats emanating from the Internet.



