2025-04-24 ジョージア工科大学
<関連情報>
- https://research.gatech.edu/spy-vs-spy-new-automated-removal-tool-can-stop-most-remote-controlled-malware
- https://www.ndss-symposium.org/ndss-paper/hitchhiking-vaccine-enhancing-botnet-remediation-with-remote-code-deployment-reuse/
- https://www.ndss-symposium.org/wp-content/uploads/2025-1353-paper.pdf
ヒッチハイク・ワクチン: リモートコード展開の再利用でボットネットの修復を強化する Hitchhiking Vaccine: Enhancing Botnet Remediation With Remote Code Deployment Reuse
Runze Zhang, Mingxuan Yao, Haichuan Xu, Omar Alrawi, Jeman Park, Brendan Saltaformaggio
Network and Distributed System Security (NDSS) Symposium February 2025
Abstract
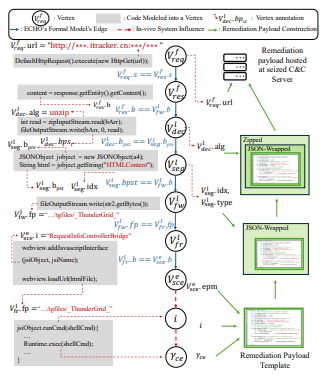
For decades, law enforcement and commercial entities have attempted botnet takedowns with mixed success. These efforts, relying on DNS sink-holing or seizing C&C infrastructure, require months of preparation and often omit the cleanup of left-over infected machines. This allows botnet operators to push updates to the bots and re-establish their control. In this paper, we expand the goal of malware takedowns to include the covert and timely removal of frontend bots from infected devices. Specifically, this work proposes seizing the malware’s built-in update mechanism to distribute crafted remediation payloads. Our research aims to enable this necessary but challenging remediation step after obtaining legal permission. We developed ECHO, an automated malware forensics pipeline that extracts payload deployment routines and generates remediation payloads to disable or remove the frontend bots on infected devices. Our study of 702 Android malware shows that 523 malware can be remediated via ECHO’s takedown approach, ranging from covertly warning users about malware infection to uninstalling the malware.