2024-04-26 カリフォルニア大学サンディエゴ校(UCSD)
 The new paper, “Pathfinder: High-Resolution Control-Flow Attacks Exploiting the Conditional Branch Predictor,” details two novel attacks that could compromise the billions of Intel processors in use.
The new paper, “Pathfinder: High-Resolution Control-Flow Attacks Exploiting the Conditional Branch Predictor,” details two novel attacks that could compromise the billions of Intel processors in use.
<関連情報>
- https://today.ucsd.edu/story/computer-scientists-unveil-novel-attacks-on-cybersecurity
- https://dl.acm.org/doi/10.1145/3620666.3651382
パスファインダー:条件分岐予測器を悪用した高解像度の制御フロー攻撃 Pathfinder: High-Resolution Control-Flow Attacks Exploiting the Conditional Branch Predictor
Hosein Yavarzadeh,Archit Agarwal,Max Christman,Christina Garman,Daniel Genkin,+ 5
ASPLOS ’24: Proceedings of the 29th ACM International Conference on Architectural Support for Programming Languages and Operating Systems Published:27 April 2024
DOI:https://doi.org/10.1145/3620666.3651382
ABSTRACT
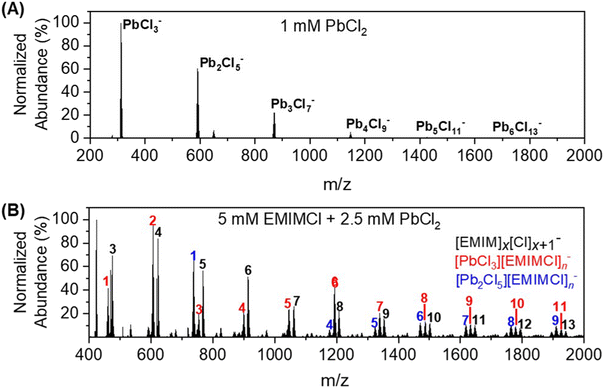
This paper introduces novel attack primitives that enable adversaries to leak (read) and manipulate (write) the path history register (PHR) and the prediction history tables (PHTs) of the conditional branch predictor in high-performance CPUs. These primitives enable two new classes of attacks: first, it can recover the entire control flow history of a victim program by exploiting read primitives, as demonstrated by a practical secret-image recovery based on capturing the entire control flow of libjpeg routines. Second, it can launch extremely high-resolution transient attacks by exploiting write primitives. We demonstrate this with a key recovery attack against AES based on extracting intermediate values.