2025-08-18 ワシントン大学セントルイス校

An example of a broken ghost gun. (Image: Raviv lab)
<関連情報>
- https://source.washu.edu/2025/08/unique-fingerprints-in-3d-printing-may-foil-adversaries/
- https://engineering.washu.edu/news/2025/Unique-fingerprints-in-3D-printing-may-foil-adversaries.html
- https://arxiv.org/abs/2403.04918
- https://arxiv.org/abs/2310.03897
法医学的3D指紋認証におけるセキュアな情報埋め込み Secure Information Embedding in Forensic 3D Fingerprinting
Canran Wang, Jinwen Wang, Mi Zhou, Vinh Pham, Senyue Hao, Chao Zhou, Ning Zhang, Netanel Raviv
arXiv last revised 3 Feb 2025 (this version, v5)
DOI:https://doi.org/10.48550/arXiv.2403.04918
Abstract
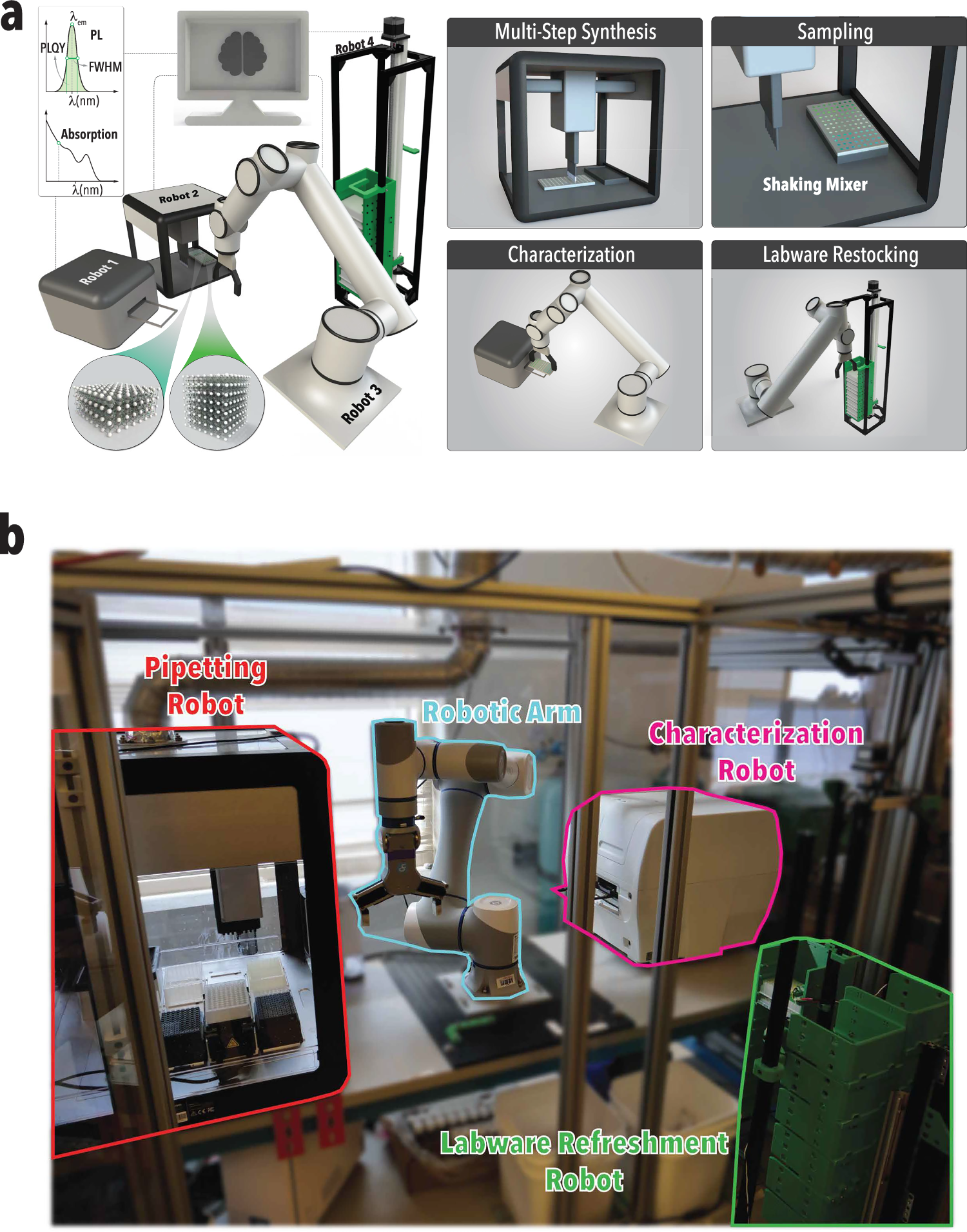
Printer fingerprinting techniques have long played a critical role in forensic applications, including the tracking of counterfeiters and the safeguarding of confidential information. The rise of 3D printing technology introduces significant risks to public safety, enabling individuals with internet access and consumer-grade 3D printers to produce untraceable firearms, counterfeit products, and more. This growing threat calls for a better mechanism to track the production of 3D-printed parts.
Inspired by the success of fingerprinting on traditional 2D printers, we introduce SIDE (\textbf{S}ecure \textbf{I}nformation Embe\textbf{D}ding and \textbf{E}xtraction), a novel fingerprinting framework tailored for 3D printing. SIDE addresses the adversarial challenges of 3D print forensics by offering both secure information embedding and extraction. First, through novel coding-theoretic techniques, SIDE is both~\emph{break-resilient} and~\emph{loss-tolerant}, enabling fingerprint recovery even if the adversary breaks the print into fragments and conceals a portion of them. Second, SIDE further leverages Trusted Execution Environments (TEE) to secure the fingerprint embedding process.
法医学的3D指紋認証のための破断耐性コード Break-Resilient Codes for Forensic 3D Fingerprinting
Canran Wang, Jin Sima, Netanel Raviv
arXiv last revised 25 Jul 2024 (this version, v2)
DOI:https://doi.org/10.48550/arXiv.2310.03897
Abstract
3D printing brings about a revolution in consumption and distribution of goods, but poses a significant risk to public safety. Any individual with internet access and a commodity printer can now produce untraceable firearms, keys, and dangerous counterfeit products. To aid government authorities in combating these new security threats, objects are often tagged with identifying information. This information, also known as fingerprints, is written into the object using various bit embedding techniques, such as varying the width of the molten thermoplastic layers. Yet, due to the adversarial nature of the problem, it is important to devise tamper resilient fingerprinting techniques, so that the fingerprint could be extracted even if the object was damaged. While fingerprinting various forms of digital media (such as videos, images, etc.) has been studied extensively in the past, 3D printing is a relatively new medium which is exposed to different types of adversarial physical tampering that do not exist in the digital world. This paper focuses on one such type of adversarial tampering, where the adversary breaks the object to at most a certain number of parts. This gives rise to a new adversarial coding problem, which is formulated and investigated herein. We survey the existing technology, present an abstract problem definition, provide lower bounds for the required redundancy, and construct a code which attains it up to asymptotically small factors. Notably, the problem bears some resemblance to the torn paper channel, which was recently studied for applications in DNA storage.