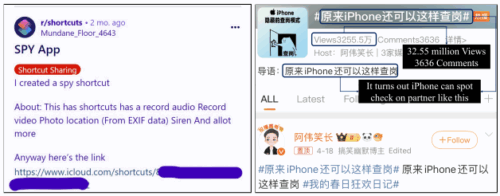
2025-08-05 ウィスコンシン大学マディソン校 (UW-Madison)
<関連情報>
- https://engineering.wisc.edu/news/uw-madison-researchers-expose-how-automation-apps-can-spy-and-how-to-detect-it/
- https://www.usenix.org/system/files/usenixsecurity25-zhang-shirley.pdf
親密なパートナー間暴力における自動化アプリの悪用可能性 Abusability of Automation Apps in Intimate Partner Violence
Shirley Zhang, Paul Chung, Jacob Vervelde, Nishant Korapati, Rahul Chatterjee, Kassem Fawaz
This paper is included in the Proceedings of the 34th USENIX Security Symposium. August 13–15, 2025 • Seattle, WA, USA
Abstract
Automation apps such as iOS Shortcuts and Android Tasker enable users to “program” new functionalities, also called recipes, on their smartphones. For example, users can create recipes to set the phone to silent mode once they arrive at their office or save a note when an email is received from a particular sender. These automation apps provide convenience and can help improve productivity. However, these automation apps can also provide new avenues for abuse, particularly in the context of intimate partner violence (IPV). This paper systematically explores the potential of automation apps to be used for surveillance and harassment in IPV scenarios. We analyze four popular automation apps — iOS Shortcuts, Samsung Modes & Routines, Tasker, and IFTTT — evaluating their capabilities to facilitate surveillance and harassment. Our study reveals that these tools can be exploited by abusers today to monitor, impersonate, overload, and control their victims. The current notification and logging mechanisms implemented in these automation apps are insufficient to warn the victim about the abuse or to help them identify the root cause and stop it. We therefore built a detection mechanism to identify potentially malicious Shortcuts recipes and tested it on 12,962 publicly available Shortcuts recipes. We found 1,014 recipes that can be used to surveil and harass others. We then discuss how users and platforms mitigate such abuse potential of automation apps.