2024-11-25 ジョージア工科大学
<関連情報>
- https://research.gatech.edu/scientists-find-vehicles-susceptible-remote-cyberattacks-award-winning-paper
- https://www.researchgate.net/publication/383876245
- file:///C:/Users/81805/Downloads/ERACAN.pdf
ERACAN:新興CAN脅威モデルからの防衛 ERACAN: Defending Against an Emerging CAN Threat Model
Zhaozhou Tang,Khaled Serag,Saman Zonouz,Z. Berkay Celik,…
Conference: 2024 ACM SIGSAC Conference on Computer and Communications Security (CCS ’24) Published:October 2024
DOI:http://dx.doi.org/10.1145/3658644.3690267
Abstract
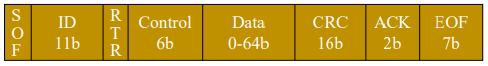
The Controller Area Network (CAN) is a pivotal communication protocol extensively utilized in vehicles, aircraft, factories, and diverse cyber-physical systems (CPSs). The extensive CAN security literature resulting from decades of wide usage may create an impression of thorough scrutiny. However, a closer look reveals its reliance on a specific threat model with a limited range of abilities. Notably, recent works show that this model is outdated and that a more potent and versatile model could soon become the norm, prompting the need for a new defense paradigm. Unfortunately, the security impact of this emerging model on CAN systems has not received sufficient attention, and the defense systems addressing it are almost nonexistent. In this paper, we introduce ERACAN, the first comprehensive defense system against this new threat model. We first begin with a threat analysis to ensure that ERACAN comprehensively understands this model’s capabilities, evasion tactics, and propensity to enable new attacks or enhance existing ones. ERACAN offers versatile protection against this spectrum of threats, providing attack detection, classification, and optional prevention abilities. We implement and evaluate ERACAN on a testbed and a real vehicle’s CAN bus to demonstrate its low latency, real-time operation, and protective capabilities. ERACAN achieves detection rates of 100% and 99.7%+ for all attacks launched by the conventional and the enhanced threat models, respectively.



